GOCDB/notifications
| Main | EGI.eu operations services | Support | Documentation | Tools | Activities | Performance | Technology | Catch-all Services | Resource Allocation | Security |
| Tools menu: | • Main page | • Instructions for developers | • AAI Proxy | • Accounting Portal | • Accounting Repository | • AppDB | • ARGO | • GGUS | • GOCDB |
| • Message brokers | • Licenses | • OTAGs | • Operations Portal | • Perun | • EGI Collaboration tools | • LToS | • EGI Workload Manager |
v5.8.0
New Features and Minor Changes
- Allow multiple email addresses to be added to the ServiceGroup contact (#146)
- Expand Write API functionality1 (#190)
- Allow access URL based changes to UI menus, colours and general config parameters (#215, #264)
- Allow "<" and ">" through service extension property validation (#221)
- Remove PHP 5.3 Support (#238)
- Add "Mx" and empty title options for users (#250)
- Initial changes allowing users to un-link their legacy Home Site (#268)
- Improvements to role request emails (#171)
- Maintainability improvements to Write API (#204, #213,#220)
- Maintainability improvements to test framework code (#208)
- Make URLs in the extension properties table clickable (#243)
Patches, Bug Fixes and Documentation Changes
- Use jquery from CDN rather than shipping it (#140)
- HTML / CSS fixes (#217, #231, #251)
- Update the regular expressions used for validation of emails (#200)
- Remove unused code (#237, #240)
- Improvement to wording used in portal (#244, #249)
- Updates to Install documentation and GitHub related files (#210, #226, #242, #258, #271).
1. For details of the new Write API functionality, please refer to the full documentation available here:
- https://wiki.egi.eu/wiki/GOCDB/Write_API/Technical_Documentation#Services
- https://wiki.egi.eu/wiki/GOCDB/Write_API/Technical_Documentation#Service_Endpoints
v5.7.6
Patches, Bug Fixes and Documentation Changes
- Fix adding roles on MariaDB
- Fix adding/editing a Site on MariaDB
- Preserve current behavior of database on MariaDB by defining character set and collation for entity tables
Full details can be found here: https://github.com/GOCDB/gocdb/milestone/5?closed=1
v5.7.5
Patches, Bug Fixes and Documentation Changes
- Trim whitespace from text entry form fields
- Add a "read-only" check to the Write API
- Add support for EGI Dev IdP "out of the box"
- Use new EGI Check-in entitlement to access GOCDB
- Write API code refactors to improve maintainability
- Use consistent wording in portal when describing downtimes
- Update to README.md in GitHub repository
Full details can be found here: https://github.com/GOCDB/gocdb/milestone/4?closed=1
v5.7.4
Patches, Bug Fixes and Documentation Changes
- Replace icons used on GOCDB pages with new icons of known source and add a 'delete' icon.
- Allow "org.squid-cache.Squid" ServiceType to be production and not monitored (https://ggus.eu/index.php?mode=ticket_info&ticket_id=139924).
- Fix GOCDB_monitor checks on SL7
- Add LICENSE file to GitHub repository
v5.7.3
Patches, Bug Fixes and Documentation Changes
- Replacement of broken Google Map with open source Leaflet map1 (https://ggus.eu/index.php?mode=ticket_info&ticket_id=137584)
- Add an Acceptable Use policy and a Privacy policy
- Enable ShibAuthToken authentication by default
- Bug fix when calculating downtime timezone offsets (https://ggus.eu/index.php?mode=ticket_info&ticket_id=130272)
- CSS and Documentation improvements.
- Spelling/Punctuation/Grammar and typo fixes
- Removal of unused files
Full details can be found here: https://github.com/GOCDB/gocdb/milestone/2?closed=1
1. this may require a change in your config/local_info.xml as follows:
Before
<google> <!-- Show google map on start page --> <show_map_on_start_page>true</show_map_on_start_page> </google>
After
<show_map_on_start_page>true</show_map_on_start_page>
v5.7
- Released: December 7th
- This release adds the following changes
- Please report issues to gocdb-admins at egi.eu
New Write API for Custom Properties
- Add/update/delete custom properties defined on Sites/Services/Endpoints using a REST API.
- Write API doc: https://wiki.egi.eu/wiki/GOCDB/Write_API/Technical_Documentation
New attributes added on ServiceEndpoint
- New boolean 'monitored' flag on SE used for ARGO monitoring.
- Adds a new 'ENDPOINT_MONITORED' element to the XML output of each endpoint in the 'get_service' method.
- New 'email' field on SE for adding contact details for that service endpoint (rather than always relying on the parent Site).
- The SE email is NOT currently rendered in the output of the 'get_service' method - this method has a Level 1 protection level which is considered a public method containing no critical information and no personal email/details: https://wiki.egi.eu/wiki/GOCDB/PI/Technical_Documentation#Protection_levels If emails are needed, we can either:
- Elevate the protection level of the get_service method to Level 2 (which means a certificate would be needed to query the method)
- Relax EGI/GOCDB protection level rules so that Level 1 can include site/service emails but no personal emails, note however there would still be a risk that personal emails would still be added.
- The SE email is NOT currently rendered in the output of the 'get_service' method - this method has a Level 1 protection level which is considered a public method containing no critical information and no personal email/details: https://wiki.egi.eu/wiki/GOCDB/PI/Technical_Documentation#Protection_levels If emails are needed, we can either:
Optional Cursor Paging on Read API
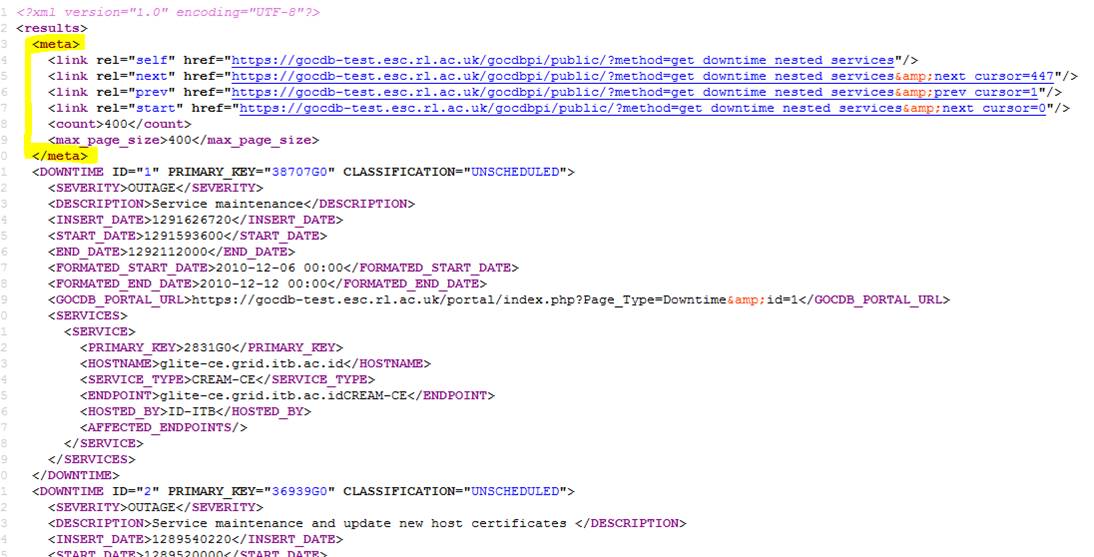
- This release applies optional CURSOR-based paging to the majority of the API methods and includes XML output changes !
- Cursor paging allows clients to iterate through massive result-sets which are split into one or more smaller pages. This allows result-sets to be processed that would otherwise be too large or memory-expensive to process in a single query.
- Paging may not always be necessary, we suggest you first try to execute your query without paging. If the query fails due to breaching of the execution time or memory limit, then try adding the next_cursor=0.
- It replaces the OFFSET-based paging that was previously available on the ‘get_downtime*’ methods due to possible data inconsistency issues when offset-paging over real-time data,
- see: https://www.sitepoint.com/paginating-real-time-data-cursor-based-pagination/
- see: https://dev.twitter.com/rest/public/timelines (explains issues with offset paging)
- Most of the API methods now support optional 'next_cursor' and 'prev_cursor' URL params.
- The following methods will not support paging: get_site_list, get_roc_list, get_service_types, get_site_count_per_country.
- For backward compatibility, pagination is disabled by default and will only be enabled when passing one of the new cursor query params.
- If neither the 'next_cursor' or 'prev_cursor' URL params are specified, the method behaves as before by fetching/rendering the requested result-set in one query, and will not add the <meta> element as detailed below.
- A non-paged query can therefore fail/timout if either the execution time or memory limits are exceeded (e.g. if you make a request for every downtime without narrowing the search with extra filter params).
- Paged XML results introduce the <meta> element which contain links to the current/self, next, previous and first page of results.
- When using paging, you need to move forward through the results by reading the next links until the ‘<count>’ element hits zero which indicates no more results are available at that particular moment in time.
- To start at the beginning of a result-set, specify 'next_cursor=0'
- The max page size has been initially set to
400100 but this is subject to change/refinement. NB: the max page size value is provided in the <max_page_size> element. - The <count> element shows how many results are on the current page (note, if this figure is less then <max_page_size> then you have come to the end of the results, and at that moment in time, the next page will show no results with a count of zero).
Changes to the Read API:
- Support for the 'page' URL parameter used for offset-paging on the 'get_downtime*' methods has been removed.
- All results are now ordered by ascending ID. NB: this changes the ‘get_downtime*’ methods which previously ordered downtimes by descending start date.
- The <meta> element is added to the XML results when paging via the 'next_cursor' or 'prev_cursor' URL params.
Here are some API queries to get you started (note that the gocdb-test data is a few weeks stale and will be updated periodically):
- https://gocdb-test.esc.rl.ac.uk/gocdbpi/public/?method=get_service&next_cursor=0
- https://gocdb-test.esc.rl.ac.uk/gocdbpi/public/?method=get_downtime_nested_services&next_cursor=0
- https://gocdb-test.esc.rl.ac.uk/gocdbpi/public/?method=get_downtime&next_cursor=0
Use of eppn in EGI
Data Privacy and Code of Conduct Policy Document Under Construction: GOCDB/data privacy
Hi Ops/all,
Apologies for the lengthy text:
With the plans to include federated identity, services like GocDB (which falls under the R&S REFEDS SP Category) will need to use an attribute supplied by an IdP to create/identify a user account, usually ‘eduPersonPrincipleName’ (eppn) (or less likely ‘eduPersonTargetedID’, eptid, see discussion below). These attributes will be used instead of an x509 DN and will require changes to the output of the PI, changing CERTDN element to PRINCIPAL element in queries like get_user and get_site_contacts - GocDB needs to republish these attributes in its PI for use by the rest of the infrastructure (e.g. queried by Ops portal, used in accounting and so on).
Now, according to the rules of the UK Access Fed (similar rules apply in other feds), “The Service Provider must not disclose to third parties any Attributes other than to any data processor of the service provider or where the relevant end user has give its prior informed consent to such disclosure. see [note2]” . (Where [note2] states: “The basic Rule is that attributes may only be used by the service requested by the user and only for the specified purposes. Service Providers that wish to use attributes in other ways (for example to provide direct user support) can arrange this either by obtaining positive informed consent from each individual End User, or by contract with Identity Providers who are then responsible for informing their End User.”)
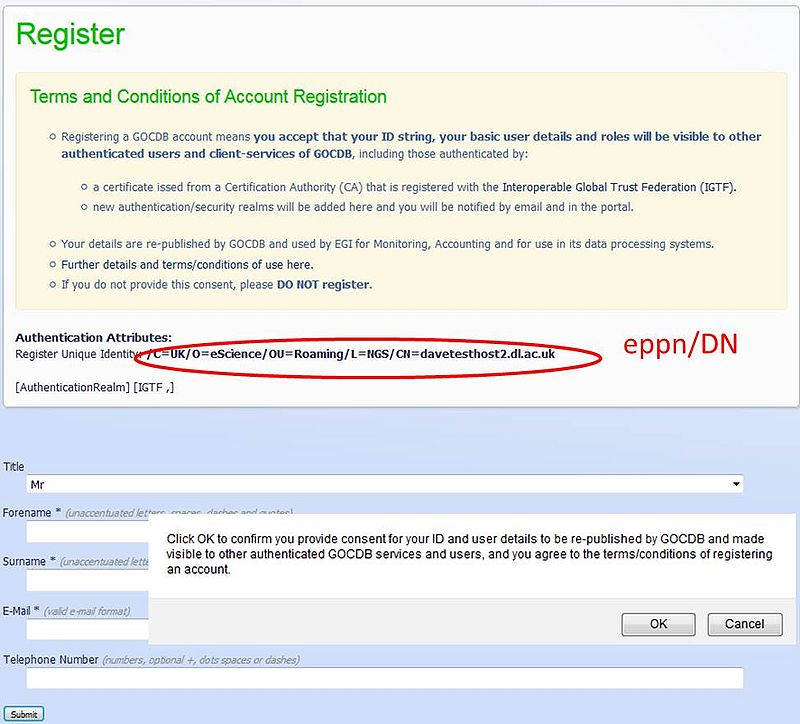
Therefore, to use Attributes like the eppn in EGI we need to obtain ‘positive informed consent’ from the user that we can publish and make visible their data/eppn to authenticated users and client-services of GOCDB, including those trusted by UK Access Management Federation, EGI-SSO or IGTF (I think we must explicitly state the different authentication/trust realms, e.g. any person/host with a valid IGTF cert can query the GocDB API for this info).
- Q. Any experts out there know if the sample notification/approval-dialog shown in the screen grab below provides adequate positive consent?
- Update, looking at: [on the definition of consent]
- Q. Assuming user clicks OK, do you know if there are any issues for EGI and for the hosting institution (STFC) in re-publishing the eppn in the PI? (it then becomes readable to any other service/user who has a valid IGTF cert)
- Update 20/08/2015: Re-publishing the eppn looks like a no-go: The SP needs to first take account of each/every IdP's policy on whether the eppn can be reused. This is does not scale. However, hashing the ePPN or using the ePUID may be ok (see below).
Using ePTID without ePPN (not suitable)
GocDB could use the ‘eduPersonTargetedID’ (eptid) and re-publish that in the PI – the eptid is less of a security concern because its anonymous/opaque. However, since the eptid will be different for the same user across different SAML Service Providers, this provides little use when there is requirement to identify a particular accountID across different SPs and organisations (this is the EGI requirement). Note, if EGI had a single centralised/proxy IdP, it could be used to re-issue the same eptid consistently to all the underlying EGI services/systems. I think this would be far preferable compared to services individually registering with federations and receiving different eptids per service.
- Update 20/08/2015, using the eptid is not suitable as it does not match the EGI requirement
Proposed Solution Requires a) and b)
- The proposed solution makes use of a a) secret salt value shared amongst project SPs to hash the ePPN, and b) uses the ePTID to solely determine if an ePPN has been re-allocated.
- Also posted here: https://community.jisc.ac.uk/groups/uk-e-infrastructure-security-access-management-wg/article/hashing-eppn-using-project-owned
a) Hashing the ePPN using a project-owned secret salt; a way to securely re-publish and correlate an ID dervied from the ePPN within a project
A group of related Service Providers, e.g. those belonging to a particular project like EGI, may concatenate a secret ‘salt’ value to the value of an attribute before hashing the result, for example; hash(‘secretSaltValue + eduPersonPrincipleName’). In doing this, the same hash value can only be reproduced if: a) an SP has access to the same secret salt value and, b) the SPs agree to use the same hashing algorithm. If the salted and hashed attribute is the ePPN, this produces an opaque and persistent identifier that can only be reproduced and correlated across the SPs within the project (i.e. those that have secure access to the salt). Provided the salt value is not disclosed to any third parties, the resulting hash string can be safely republished, for example, for use in correlating account IDs across project-specific SPs in the same project.
b) Requesting both ePPN and ePTID to determine ePPN re-allocation
The ePPN is re-assignable, and re-assignment practices depend on the federation/country; you cannot always rely on a federation re-assigning an ePPN after an agreed period of inactivity (e.g. 2yrs with the UKAMF). Therefore, as suggested by the R&S REFEDS SP Category, its good practice to also request/release both ePPN and ePTID together. This is useful because the SP can also record an ePTID change (by definition the ePTID can never be re-assigned). By doing this, the SP knows that the holder of the ePPN has changed. Note, the ePTID would only be used internally by a particular SP to check that the user has not changed; it wouldn't be used when hashing the ePPN with a secret salt for use in republishing as described above.
- Q. I think this could be used by SPs within EGI allowing accounts to be safely correlated across SPs.
I’d be grateful for any thoughts/guidance on these matters (many thanks to Mikael Linden and Andrew Cormack for their help).
Cheers,
David
v5.5 Release
- Test instance: https://gocdb-test.esc.rl.ac.uk/portal
- Release date was Wed 2nd Dec.
- The 'get_site_security_info' method will be moved from 'private,' which requires the DN of each calling client to be manually registered in an ACL (access control list), to 'protected,' which allows anyone with a valid IGTF certificate to query the method. The only info regarded as potentially sensitive is each NGI's CSIRT email and Tel. The reasons why this method was originally made private were a) because it collates all the contacts into a single query and so was largely a spam concern, b) inherited legacy - it's simply always been this way. I also understand that the original intention was that the generic CSIRT email addresses/Tels were never intended to be restricted.
- Adding <SCOPES/> element to the XML output of the following PI queries: get_site, get_service, get_service_endpoint, get_ngi, get_service_group
Adding new scope tags for WLCG VOs, including ‘wlcg, atlas, cms, lhcb, alice, tier1, tier2’ for finer-grained resource filtering.- Large scale refactoring of the role model to cater for multi-tenant (multiple projects) and to more easily add/refine new roles and actions/permissions per-project. The main change is that roles apply to a particular project – this is shown in the output of the ‘get_user’ method that qualifies which user-roles apply to which project using the ‘<RECOGNISED_IN_PROJECTS>’ element.
- For example, see the example XML below and notice that I have roles in two different projects.
- Note also that some roles are project agnostic such as ServiceGroup roles - ServiceGroups simply group existing servcies together across different sites and projects, and so SGs don't have an affiliation to a Project.
- For the current production deployment, there is only a single project (EGI), so in reality this shouldn’t add much complexity. However, if we introduce new projects in the future, it is important to understand which roles apply in which project.
- Role to Action mappings given in the 'Role Action Map' view, see https://gocdb-test.esc.rl.ac.uk/portal/index.php?Page_Type=View_Role_Action_Mappings
- e.g. https://gocdb-test.esc.rl.ac.uk/gocdbpi/public/?method=get_user&surname=Meredith
<results>
<EGEE_USER ID="1484G0" PRIMARY_KEY="1484G0">
<FORENAME>David</FORENAME>
<SURNAME>Meredith</SURNAME>
<TITLE>Dr</TITLE>
<DESCRIPTION/>
<GOCDB_PORTAL_URL>https://gocdb-test.esc.rl.ac.uk/portal/index.php?Page_Type=User;ampid=1484</GOCDB_PORTAL_URL>
<EMAIL>david.meredith@stfc.ac.uk</EMAIL>
<TEL>+44 1925 603762</TEL>
<WORKING_HOURS_START/>
<WORKING_HOURS_END/>
<CERTDN>/C=UK/O=eScience/OU=CLRC/L=DL/CN=david meredith</CERTDN>
<SSOUSERNAME>davidm</SSOUSERNAME>
<APPROVED/>
<ACTIVE/>
<HOMESITE/>
<USER_ROLE>
<USER_ROLE>Service Group Administrator</USER_ROLE>
<ON_ENTITY>OPSTOOLS</ON_ENTITY>
<ENTITY_TYPE>servicegroup</ENTITY_TYPE>
<PRIMARY_KEY>722G0</PRIMARY_KEY>
<RECOGNISED_IN_PROJECTS/> <!-- ***new element (ServiceGroup role is Project agnostic)*** -->
</USER_ROLE>
<USER_ROLE>
<USER_ROLE>Chief Operations Officer</USER_ROLE>
<ON_ENTITY>StandaloneProjectX</ON_ENTITY>
<ENTITY_TYPE>project</ENTITY_TYPE>
<PRIMARY_KEY>1505</PRIMARY_KEY>
<RECOGNISED_IN_PROJECTS> <!-- ***new element*** -->
<PROJECT ID="1505">StandaloneProjectX</PROJECT>
</RECOGNISED_IN_PROJECTS>
</USER_ROLE>
<USER_ROLE>
<USER_ROLE>Site Operations Manager</USER_ROLE>
<ON_ENTITY>GRIDOPS-GOCDB</ON_ENTITY>
<ENTITY_TYPE>site</ENTITY_TYPE>
<PRIMARY_KEY>123G0</PRIMARY_KEY>
<RECOGNISED_IN_PROJECTS> <!-- ***new element*** -->
<PROJECT ID="1">EGI</PROJECT>
</RECOGNISED_IN_PROJECTS>
</USER_ROLE>
<USER_ROLE></USER_ROLE>
</EGEE_USER>
</results>
- Lots of other changes in the Dev changelog (but these don't affect the PI): (https://github.com/GOCDB/gocdb/blob/dev/changeLog.txt )