Difference between revisions of "Virtual Machine Image Endorsement"
(→Ubuntu) |
|||
| (30 intermediate revisions by 3 users not shown) | |||
| Line 23: | Line 23: | ||
|- | |- | ||
| EGI | | EGI | ||
| General purpose images. Based on | | General purpose images. Based on broadly used OSes | ||
| EGI | | EGI | ||
|- | |- | ||
| Line 33: | Line 33: | ||
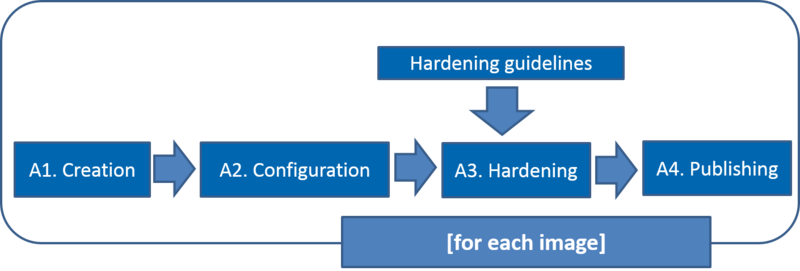
= Activities and workflow = | = Activities and workflow = | ||
[[File:Endorsement-workflow-process.png| | [[File:Endorsement-workflow-process.png|800px]] | ||
{| class="wikitable" | {| class="wikitable" | ||
| Line 55: | Line 55: | ||
|} | |} | ||
= Documents and Policies = | |||
Policies are defined by the SPG group and are published in the https://wiki.egi.eu/wiki/SPG:Documents | |||
It is particularly relevant the [https://documents.egi.eu/document/771 Security Policy for the Endorsement and Operation of Virtual Machine Images] and a [https://wiki.egi.eu/wiki/SPG:Drafts:Virtualisation_Policy draft of a Virtualisation Policy]. | |||
[https://wiki.egi.eu/wiki/SPG:Drafts SPG Drafts under development] | |||
= Hardening guidelines = | |||
Checklist kindly provided by David Groep. CSIRT working on official guidelines. | |||
== Securing services == | |||
Follow the best practice guides for each service that's offered to the outside world. For instance, guides for: | |||
*[http://wiki.centos.org/HowTos/Network/SecuringSSH SSH] | |||
*[https://www.owasp.org/index.php/Securing_tomcat Tomcat] | |||
== Configuration == | == Configuration == | ||
* Delete any credential, passwords, accounts or X509 certificate/proxy | |||
* Disable all services unless necessary for the intended tasks | |||
* Make sure that all installed services don't use default passwords and accounts | |||
* Make sure the firewall config (iptables for Linux, also on IPv6) is minimally open: only SSH and required services | |||
* SSH: disable password authentication (a SSH key should be configured during contextualisation) | |||
For more details, see [https://aws.amazon.com/whitepapers/aws-security-best-practices/ AWS Security Best Practices], in particular Creating Custom AMIs, page 41+ | |||
== Vulnerability assessment == | |||
Instantiate the image on a local network (without global connectivity) and run vulnerability assessment tools against it. | |||
* From within the running VM image and quickly do some of the configuration checks is [https://cisofy.com/lynis/ Lynis] (working for most Unix/Linux flavours): which automates some of the testing of ssh/http/startup/etc configuration. Unpacking and running as root "./lynis --debug audit system" will give a wealth of hints and data. Many of these are hardening hints, so are not direct vulnerabilities, but merit review and warnings should be explainable. | |||
* From outside the VM, Run Nmap - it should show only intended open ports on the network. Try "sudo nmap -p- -sV -T5 192.168.0.103" and do that for both UDP and TCP. It should be rather quiet ... except for intended ports (a web site does need port 80 and 443 to be open). | |||
*install an [http://openvas.org/ OpenVAS] machine on the same subnet and probe a running instance of the image | |||
*[http://www.metasploit.com/ Metasploit] can try all possible exploits against your new VM from an adjancent machine | |||
*if it's an RPM-package based system, run [http://pakiti.sourceforge.net/ Pakiti] against it. Debian currently does not provide approved data in CVE format. | |||
== Web applications == | |||
For web applications, run one or more of | |||
*[http://www.cirt.net/nikto2/ Nikto] | |||
*[http://sqlmap.org/ SQLmap] to find SQL injection points | |||
*[http://www.arachni-scanner.com/ Arachni] finds XSS and XSRF exploits in web frameworks (works better when installed independently, not as part of OpenVAS). | |||
Then explain notices on the false positives that are there. | |||
= Publishing = | |||
When publishing, each image will bring its own tags and metadata in AppDB (TBD). | |||
[https://wiki.appdb.egi.eu/main:faq:how_to_register_a_virtual_appliance Registering appliance] | |||
[https://wiki.appdb.egi.eu/main:guides:guide_for_managing_virtual_appliance_versions_using_the_portal Managing appliance] | |||
[https://wiki.egi.eu/wiki/ | [https://wiki.egi.eu/wiki/EGI_AppDB_REST_API_v1.0 APPDB REST API] | ||
= | = Continuous improvement = | ||
It is important to understand how much each image is used. The "popularity" of a given image can be: | |||
*most downloaded (AppDB) | |||
*most used (accounting) | |||
Also important to have feedback from CSIRT on each image to understand if the procedure is effective. | |||
= Procedures for EGI images = | = Procedures for EGI images = | ||
| Line 100: | Line 150: | ||
|} | |} | ||
== Ubuntu | == Ubuntu 12 and Ubuntu 14 == | ||
=== Creation === | === Creation === | ||
Ubuntu images are create from the net install images with minimal installations. Once installed, the packages '''MUST ''' be upgraded to the latest version available. Size of the image should be as small as possible (recommended below 1.5GB) to ease distribution. | |||
Extra packages to install (from the basic installation): | |||
* cloud-init | |||
* curl | |||
See https://github.com/EGI-FCTF/VMI-endorsement/tree/master/ubuntu for a [http://www.packer.io Packer] configuration to build and configure such images | |||
=== Configuration === | === Configuration === | ||
* General | |||
** No running services apart from sshd | |||
** root password must be disabled | |||
* sshd ([https://github.com/EGI-FCTF/VMI-endorsement/blob/master/ubuntu/provisioners/sshd_config sample sshd configuration]) | |||
** root login '''must''' be disabled | |||
** password logins '''must''' be disabled | |||
* Cloud-init ([https://github.com/EGI-FCTF/VMI-endorsement/blob/master/ubuntu/provisioners/cloud.cfg sample cloud-init configuration]) | |||
** No sources should be specified to allow the different sources from OpenNebula/OpenStack/Synnefo to work with the VM | |||
** Root should be disabled | |||
** Passwords should not be used | |||
** Should enable partition grow (enable grow part and resizefs) | |||
** Should enable package installation (enable package-update-upgrade-install) | |||
=== Hardening === | === Hardening === | ||
Only service running is SSH. | |||
TODO: add firewall configuration in Ubuntu | |||
=== Publishing === | === Publishing === | ||
Image must be published as OVA package including: | |||
* disk image as VMDK | |||
* OVF description of the VM Image | |||
OVA should be uploaded to the EGI Appliance Repository at http://appliance-repo.egi.eu/images/EGI-endorsed/ubuntu/ and named as follows: | |||
ubuntu-14.04-YYYYMMDD.ova | |||
or | |||
ubuntu-12.04-YYYYMMDD.ova | |||
where <code>YYYYMMDD</code> is the date of creation. | |||
The image will be linked into AppDB at the https://appdb.egi.eu/store/vappliance/egi.ubuntu.14.04 and https://appdb.egi.eu/store/vappliance/egi.ubuntu.12.04 | |||
Image '''must''' be updated for every security update related with the base system. | |||
== | == CentOS6 == | ||
=== Hardening | === Creation === | ||
CentOS provides minimal images (e.g. net install images) that allow to perform minimal installations. These should be used as basis for the creation of images to avoid large image sizes and the installation of non-needed software. Once installed, the packages '''MUST ''' be upgrade to the latest version available. Size of the image should be as small as possible (recommended below 1.5GB) to ease distribution. | |||
Extra packages to install (from the basic installation): | |||
* epel | |||
* cloud-init | |||
* openssh-clients | |||
See https://github.com/EGI-FCTF/VMI-endorsement/tree/master/centos for a [http://www.packer.io Packer] configuration to build and configure such image. | |||
=== Configuration === | |||
* General | |||
** No running services apart from sshd | |||
** root password must be disabled | |||
* sshd ([https://github.com/EGI-FCTF/VMI-endorsement/blob/master/centos/6/provisioners/sshd_config sample sshd configuration]) | |||
** root login '''must''' be disabled | |||
** password logins '''must''' be disabled | |||
* Cloud-init ([https://github.com/EGI-FCTF/VMI-endorsement/blob/master/centos/6/provisioners/cloud.cfg sample cloud-init configuration]) | |||
** No sources should be specified to allow the different sources from OpenNebula/OpenStack/Synnefo to work with the VM | |||
** Root should be disabled | |||
** Passwords should not be used | |||
** Should enable partition grow (enable grow part and resizefs) | |||
** Should enable package installation (enable package-update-upgrade-install) | |||
=== Hardening === | |||
CentOS default installation already comes with firewall enabled, configuration as described above should be ok for SSH. | |||
Postfix is running in the VM (dependency of cron and cloud-init), but only listens on localhost. | |||
TODO: fix firewall configuration in CentOS 6. | |||
=== Publishing === | |||
Image must be published as OVA package including: | |||
* disk image as VMDK | |||
* OVF description of the VM Image | |||
OVA should be uploaded to the EGI Appliance Repository at http://appliance-repo.egi.eu/images/EGI-endorsed/centos/6/ and named as follows: | |||
centos-6-YYYYMMDD.ova | |||
where <code>YYYYMMDD</code> is the date of creation. | |||
The image will be linked into AppDB at the https://appdb.egi.eu/store/vappliance/egi.centos.6 | |||
Image '''must''' be updated for every security update related with the base system. | |||
= Procedures for VO images = | = Procedures for VO images = | ||
The procedure is similar as to EGI images, but a VO expert (endorser) is fully responsible for the process of the endorsement of a specific VM. For the fedcloud.egi.eu VO the VO expert will get special help from EGI experts. | The procedure is similar as to EGI images, but a VO expert (endorser) is fully responsible for the process of the endorsement of a specific VM. For the fedcloud.egi.eu VO the VO expert will get special help from EGI experts. | ||
= References = | |||
[https://wiki.egi.eu/wiki/AppDB AppDB] | |||
Latest revision as of 13:02, 24 October 2017
Description
Goal
Set up a process assuring that a Virtual Machine Image (VMI)/ Virtual Appliance (VA) published in AppDB is well-configured, secure and up-to-date.
Members
- Enol Fernandez [EF]
- Vincenzo Spinoso [VS]
Contacts
SSO group available: vm-image-endorsement@mailman.egi.eu
Image types
| Type | Description | Managed by |
|---|---|---|
| EGI | General purpose images. Based on broadly used OSes | EGI |
| VO-specific | VO specific images, available to a specific VO and customized for specific purposes | VO-expert |
Activities and workflow
| Activity | Description |
|---|---|
| A1. Creation | Set up an image ready to be used by a Resource Provider |
| A2. Configuration | Configuration assures that packages are up to date and no wrong default configurations are left for any applications/services |
| A3. Hardening | Security is provided by applying CSIRT guidelines for the VMI Endorsement |
| A4. Publishing | Make image available on AppDB with proper tags, metadata, links |
Documents and Policies
Policies are defined by the SPG group and are published in the https://wiki.egi.eu/wiki/SPG:Documents
It is particularly relevant the Security Policy for the Endorsement and Operation of Virtual Machine Images and a draft of a Virtualisation Policy.
Hardening guidelines
Checklist kindly provided by David Groep. CSIRT working on official guidelines.
Securing services
Follow the best practice guides for each service that's offered to the outside world. For instance, guides for:
Configuration
- Delete any credential, passwords, accounts or X509 certificate/proxy
- Disable all services unless necessary for the intended tasks
- Make sure that all installed services don't use default passwords and accounts
- Make sure the firewall config (iptables for Linux, also on IPv6) is minimally open: only SSH and required services
- SSH: disable password authentication (a SSH key should be configured during contextualisation)
For more details, see AWS Security Best Practices, in particular Creating Custom AMIs, page 41+
Vulnerability assessment
Instantiate the image on a local network (without global connectivity) and run vulnerability assessment tools against it.
- From within the running VM image and quickly do some of the configuration checks is Lynis (working for most Unix/Linux flavours): which automates some of the testing of ssh/http/startup/etc configuration. Unpacking and running as root "./lynis --debug audit system" will give a wealth of hints and data. Many of these are hardening hints, so are not direct vulnerabilities, but merit review and warnings should be explainable.
- From outside the VM, Run Nmap - it should show only intended open ports on the network. Try "sudo nmap -p- -sV -T5 192.168.0.103" and do that for both UDP and TCP. It should be rather quiet ... except for intended ports (a web site does need port 80 and 443 to be open).
- install an OpenVAS machine on the same subnet and probe a running instance of the image
- Metasploit can try all possible exploits against your new VM from an adjancent machine
- if it's an RPM-package based system, run Pakiti against it. Debian currently does not provide approved data in CVE format.
Web applications
For web applications, run one or more of
- Nikto
- SQLmap to find SQL injection points
- Arachni finds XSS and XSRF exploits in web frameworks (works better when installed independently, not as part of OpenVAS).
Then explain notices on the false positives that are there.
Publishing
When publishing, each image will bring its own tags and metadata in AppDB (TBD).
Continuous improvement
It is important to understand how much each image is used. The "popularity" of a given image can be:
- most downloaded (AppDB)
- most used (accounting)
Also important to have feedback from CSIRT on each image to understand if the procedure is effective.
Procedures for EGI images
| Activity | Initial activity | Ongoing activity |
|---|---|---|
| A1. Creation | Set up the procedure for a given image | Use the procedure to create/update the image according to a given policy (on security issue, on request, every X days… ) |
| A2. Configuration | Create VMI configuration procedure for a given image | Apply VMI configuration procedure to a given image |
| A3. Hardening | Create VMI hardening procedure for a given image based on guidelines | Apply VMI hardening procedure to a given image |
| A4. Publishing | Publish the image on AppDB | Publish the image on AppDB |
Ubuntu 12 and Ubuntu 14
Creation
Ubuntu images are create from the net install images with minimal installations. Once installed, the packages MUST be upgraded to the latest version available. Size of the image should be as small as possible (recommended below 1.5GB) to ease distribution.
Extra packages to install (from the basic installation):
- cloud-init
- curl
See https://github.com/EGI-FCTF/VMI-endorsement/tree/master/ubuntu for a Packer configuration to build and configure such images
Configuration
- General
- No running services apart from sshd
- root password must be disabled
- sshd (sample sshd configuration)
- root login must be disabled
- password logins must be disabled
- Cloud-init (sample cloud-init configuration)
- No sources should be specified to allow the different sources from OpenNebula/OpenStack/Synnefo to work with the VM
- Root should be disabled
- Passwords should not be used
- Should enable partition grow (enable grow part and resizefs)
- Should enable package installation (enable package-update-upgrade-install)
Hardening
Only service running is SSH. TODO: add firewall configuration in Ubuntu
Publishing
Image must be published as OVA package including:
- disk image as VMDK
- OVF description of the VM Image
OVA should be uploaded to the EGI Appliance Repository at http://appliance-repo.egi.eu/images/EGI-endorsed/ubuntu/ and named as follows:
ubuntu-14.04-YYYYMMDD.ova
or
ubuntu-12.04-YYYYMMDD.ova
where YYYYMMDD is the date of creation.
The image will be linked into AppDB at the https://appdb.egi.eu/store/vappliance/egi.ubuntu.14.04 and https://appdb.egi.eu/store/vappliance/egi.ubuntu.12.04
Image must be updated for every security update related with the base system.
CentOS6
Creation
CentOS provides minimal images (e.g. net install images) that allow to perform minimal installations. These should be used as basis for the creation of images to avoid large image sizes and the installation of non-needed software. Once installed, the packages MUST be upgrade to the latest version available. Size of the image should be as small as possible (recommended below 1.5GB) to ease distribution.
Extra packages to install (from the basic installation):
- epel
- cloud-init
- openssh-clients
See https://github.com/EGI-FCTF/VMI-endorsement/tree/master/centos for a Packer configuration to build and configure such image.
Configuration
- General
- No running services apart from sshd
- root password must be disabled
- sshd (sample sshd configuration)
- root login must be disabled
- password logins must be disabled
- Cloud-init (sample cloud-init configuration)
- No sources should be specified to allow the different sources from OpenNebula/OpenStack/Synnefo to work with the VM
- Root should be disabled
- Passwords should not be used
- Should enable partition grow (enable grow part and resizefs)
- Should enable package installation (enable package-update-upgrade-install)
Hardening
CentOS default installation already comes with firewall enabled, configuration as described above should be ok for SSH. Postfix is running in the VM (dependency of cron and cloud-init), but only listens on localhost.
TODO: fix firewall configuration in CentOS 6.
Publishing
Image must be published as OVA package including:
- disk image as VMDK
- OVF description of the VM Image
OVA should be uploaded to the EGI Appliance Repository at http://appliance-repo.egi.eu/images/EGI-endorsed/centos/6/ and named as follows:
centos-6-YYYYMMDD.ova
where YYYYMMDD is the date of creation.
The image will be linked into AppDB at the https://appdb.egi.eu/store/vappliance/egi.centos.6
Image must be updated for every security update related with the base system.
Procedures for VO images
The procedure is similar as to EGI images, but a VO expert (endorser) is fully responsible for the process of the endorsement of a specific VM. For the fedcloud.egi.eu VO the VO expert will get special help from EGI experts.