Difference between revisions of "Federated Cloud Architecture"
(→OCCI) |
|||
| Line 15: | Line 15: | ||
OCCI’s specification consists of three basic elements, each covered in a separate specification document: | OCCI’s specification consists of three basic elements, each covered in a separate specification document: | ||
'''OCCI Core''' describes the formal definition of the OCCI Core Model <ref>R. Nyren, A. Edmonds, A. Papaspyrou, and T. Metsch, | '''OCCI Core''' describes the formal definition of the OCCI Core Model <ref>R. Nyren, A. Edmonds, A. Papaspyrou, and T. Metsch, Open Cloud Computing Interface - Core, GFD-P-R.183, April 2011. [Online]. Available: http://ogf.org/documents/GFD.183.pdf </ref>. '''OCCI HTTP Rendering''' defines how to interact with the OCCI Core Model using the RESTful OCCI API <ref>T. Metsch and A. Edmonds, Open Cloud Computing Interface - HTTP Rendering, GFD-P-R.185, April 2011. [Online]. Available: http://ogf.org/documents/GFD.185.pdf</ref>. The document defines how the OCCI Core Model can be communicated and thus serialised using the HTTP protocol. OCCI Infrastructure contains the definition of the '''OCCI Infrastructure''' extension for the IaaS domain <ref>Open Cloud Computing Interface - Infrastructure, GFD-P-R.184, April 2011. [Online]. Available: http://ogf.org/documents/GFD.184.pdf</ref>. The document defines additional resource types, their attributes and the actions that can be taken on each resource type. Detailed description of the abovementioned elements of the specification is outside the scope of this document. A simplified description is as follows. | ||
OCCI Core defines base types '''Resource''', '''Link''', '''Action''' and '''Mixin'''. Resource represents all OCCI objects that can be manipulated and used in any conceivable way. In general, it represents provider’s resources such as images (Storage Resource), networks (Network Resource), virtual machines (Compute Resource) or available services. Link represents a base association between two Resource instances; it indicates a generic connection between a source and a target. The most common real world examples are Network Interface and Storage Link connecting Storage and Network Resource to a Compute Resource. Action defines an operation that may be invoked, tied to a specific Resource instance or a collection of Resource instances. In general, Action is designed to perform complex high-level operations | OCCI Core defines base types '''Resource''', '''Link''', '''Action''' and '''Mixin'''. Resource represents all OCCI objects that can be manipulated and used in any conceivable way. In general, it represents provider’s resources such as images (Storage Resource), networks (Network Resource), virtual machines (Compute Resource) or available services. Link represents a base association between two Resource instances; it indicates a generic connection between a source and a target. The most common real world examples are Network Interface and Storage Link connecting Storage and Network Resource to a Compute Resource. Action defines an operation that may be invoked, tied to a specific Resource instance or a collection of Resource instances. In general, Action is designed to perform complex high-level operations | ||
Revision as of 10:05, 8 June 2015
| Overview | For users | For resource providers | Infrastructure status | Site-specific configuration | Architecture |
Cloud Interfaces
To federate a cloud system there are several functions for which a common interface must be defined. These are each described below and overall provide the definition of the method by which a ‘user’ of the service would be able to interact.
VM Management
VM management allows users to run on demand any kind of workloads on virtual machines. Community cloud federations may chose any interoperable interface within their community to provide VM Management. The Public Federated Cloud uses the OCCI open standard for this purpose.
OCCI
The Open Cloud Computing Interface (OCCI) is a RESTful Protocol and API designed to facilitate interoperable access to, and query of, cloud-based resources across multiple resource providers and heterogeneous environments. The formal specification is maintained and actively worked on by OGF’s OCCI-WG, for details see http://occi-wg.org/.
OCCI’s specification consists of three basic elements, each covered in a separate specification document: OCCI Core describes the formal definition of the OCCI Core Model [1]. OCCI HTTP Rendering defines how to interact with the OCCI Core Model using the RESTful OCCI API [2]. The document defines how the OCCI Core Model can be communicated and thus serialised using the HTTP protocol. OCCI Infrastructure contains the definition of the OCCI Infrastructure extension for the IaaS domain [3]. The document defines additional resource types, their attributes and the actions that can be taken on each resource type. Detailed description of the abovementioned elements of the specification is outside the scope of this document. A simplified description is as follows.
OCCI Core defines base types Resource, Link, Action and Mixin. Resource represents all OCCI objects that can be manipulated and used in any conceivable way. In general, it represents provider’s resources such as images (Storage Resource), networks (Network Resource), virtual machines (Compute Resource) or available services. Link represents a base association between two Resource instances; it indicates a generic connection between a source and a target. The most common real world examples are Network Interface and Storage Link connecting Storage and Network Resource to a Compute Resource. Action defines an operation that may be invoked, tied to a specific Resource instance or a collection of Resource instances. In general, Action is designed to perform complex high-level operations changing the state of the chosen Resource such as virtual machine reboot or migration. The concept of mixins is used to facilitate extensibility and provide a way to define provider-specific features.
The VM Management scenario page contains detailed information on the support for OCCI on different Cloud Management Stacks.
OCCI extensions for FedCloud
Contextualization is the process of installing, configuring and preparing software upon boot time on a pre-defined virtual machine image (e.g. setting the hostname, IP addresses, SSH authorized keys, starting services, installing applications, etc.). OCCI v1.1 (current version of the standard) lacks of mechanisms to allow this contextualization of VMs, hence we have proposed the use of a new OCCI mixins that have attributes to hold user-provided data with the context information for the VM.
The mixins are:
| term | scheme | attributes |
|---|---|---|
user_data
|
http://schemas.openstack.org/compute/instance#
|
org.openstack.compute.user_data: string that holds base64 encoded data to be available at the VM upon instantiation
|
public_key
|
http://schemas.openstack.org/instance/credentials#
|
org.openstack.credentials.publickey.name: string with the name of the public key (optional)org.openstack.credentials.publickey.data: string with the public key
|
Each Cloud Management stack provides its own mechanisms to make these data available at the VM. FedCloud recommends using cloud-init for handling the data. Cloud-init frees the user from managing the specific ways for handling the contextualization information and it's widely available in most OS versions and IaaS cloud platforms. By default cloud-init will:
- Put the ssh-key into the ~/.ssh/authorized_keys of root user (or equivalent)
- If the user provided data is a script, it will be executed upon instantiation.
More complex use-cases are supported, with documented examples in regular cloud-init documentation.
Data management
The Data management provides a data infrastructure for storing and retrieving data from anywhere at any time. Community cloud federations may chose any interoperable interface within their community to provide Data Management capabilities. The Public Federated Cloud uses the CDMI open standard for this purpose.
CDMI
The SNIA Cloud Data Management Interface (CDMI)[4] defines a RESTful open standard for operations on storage objects. Semantically the interface is very close to AWS S3 and MS Azure Blob, but is more open and flexible for implementation.
CDMI offers clients a way for operating both on a storage management system and single data items. The exact level of support depends on the concrete implementation and is exposed to the client as part of the protocol.The design of the protocol is aimed both at flexibility and efficiency. Certain heavyweight operations, e.g. blob download, can be performed also with a pure HTTP client to make use of the existing ecosystem of tools. CDMI is built around the concept of Objects, which vary in supported operations and metadata schema. Each Object has an ID, which is unique across all CDMI deployments.
There are 4 CDMI objects most relevant in the context of EGI’s Federated Cloud:
- Data object: Abstraction for a file with rich metadata.
- Container: Abstraction for a folder. Export to non-HTTP protocols is performed on the container level. Container might have other containers inside of them.
- Capability: Exposes information about a feature set of a certain object. CDMI supports partial implementation of the standards by defining optional features and parameters. In order to discover what functionality is supported by a specific implementation, CDMI client can issue a GET request to a fixed url: /cdmi_capabilities.
- Domain: Deployment specific information.
Attachment of the storage items to a VM can often be performed more efficiently using protocols like NFS or iSCSI. CDMI supports exposing of this information via container metadata. A client can make use of this information to attach a storage item to a VM over an OCCI protocol.
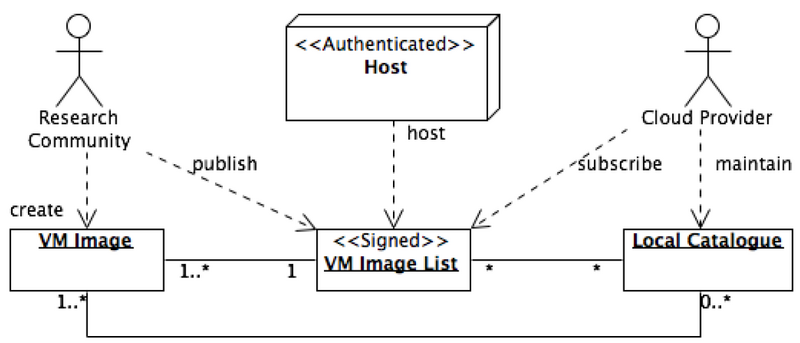
VM Image management
In a distributed, federated Cloud infrastructure, users will often face the situation of efficiently managing and distributing their VM Images across multiple resource providers. The VM Image management subsystem provides the user with an interface into the EGI Cloud Infrastructure Platform to notify supporting resource providers of the existence of a new or updated VM Image. Sites then examine the provided information, and pending their decision pool the new or updated VM Image locally for instantiation.
This concept introduces a number of capabilities into the EGI Cloud Infrastructure Platform:
- VM Image lifecycle management – Apply best practices of Software Lifecycle Management at scale across EGI
- Automated VM Image distribution – Publish VM images (or updates to existing images) once, while they are automatically distributed to the Cloud resource providers that support the publishing research community with Cloud resources.
- Asynchronous distribution mechanism – Publishing images and pooling these locally are intrinsically decoupled, allowing federated Resource Providers to apply local, specific processes transparently before VM images are available for local instantiation, for example:
- Provider-specific VM image endorsement policies – Not all federated Cloud resource providers will be able to enforce strict perimeter protection in their Cloud infrastructure as risk management to contain potential security incidents related to VM images and instances. Sites may implement a specific VM Image inspection and assessment policy prior to pooling the image for immediate instantiation.
Two command-line tools provide the principal functionality of this subsystem; “vmcaster” to publish VM image lists and “vmcatcher” to subscribe to changes to these lists, respectively.
Research Communities ultimately create and update VM Images (or delegate this functionality). The Images themselves are stored in Appliance repositories that are provided and managed elsewhere, typically by the Research Community itself.
A representative of the Research Community then generates a VM Image list (or updates an existing one) and publishes it on an authenticated host, which is typically using a host certificate signed by a CA included in the EGI Trust Anchor profile.
Federated Clouds Resource Provider then subscribe to changes in VM Image lists by regularly downloading the list from the authenticated host, and comparing it against local copies. New and updated VM Images are downloaded from the appliance repository referenced in the VM Image list into a local staging cache and, where required, made available for further examination and assessment.
Ultimately, Cloud resource Providers will make VM Images available for immediate instantiation by the Research Community.
EGI Core services integration
Virtual Organisation Management & AAI: VOMS
Within EGI, research communities are generally identified and, for the purpose of using EGI resources, managed through “Virtual Organisations” (VOs). The Public EGI Cloud currently also uses VOs for authorization and authentication. Three VOs must be supported at every Resource Provider:
opsVO, used for monitoring purposes;dteamVO, used for testing purposes by site operators; andfedcloud.egi.euVO, a catch-all VO that provides resources to users for a limited period of time (6 months initially) for protopying and validation.
Resource Providers may support additional VOs in order to give access to other user communities.
Integration modules are available for each Cloud Management Framework that been developed by the task members. Configuring these modules into a provider’s cloud installation will allow members of these VOs to access the cloud. The user retrieves a VOMS attribute certificate from the VOMS server of the desired VO (currently, Perun server for fedcloud.egi.eu VO) and thus creates a local VOMS proxy certificate. The VOMS proxy certificate is use in subsequent calls to the OCCI endpoints of OpenNebula or OpenStack using the rOCCI client tool. The rOCCI client directly talks to OpenNebula endpoints, which map the certificate and VO information to local users. Local users need to have been created in advance, which is triggered by regular synchronizations of the OpenNebula installation with Perun.
In order to access an OpenStack OCCI endpoint, the rOCCI client needs to retrieve a Keystone token from OpenStack Keystone first. The retrieval is transparent to the user and automated in the workflow of accessing the OpenStack OCCI endpoint. It is triggered by the OCCI endpoint rejecting invalid requests and sending back an HTTP header referencing the Keystone URL for authentication. Users are generated on the fly in Keystone, it does not need regular synchronization with the VO Management server Perun.
Generic information about how to configure VOMS support for the supported Cloud Management Frameworks is available at MAN10. Information to how to add the support for a new Virtual Organisation on the EGI Federated Cloud can be found at HOWTO16.
Information discovery: BDII
Users and tools can discover the available resource in the infrastructure by querying EGI information discovery services. The common information system deployed at EGI is based on the Berkeley Database Information Index (BDII) with a hierarchical structure distributed over the whole infrastructure.
The information system is structured in three levels: the services publish their information (e.g. specific capabilities, total and available capacity or user community supported by the service) using an OGF recommended standard format, GLUE2[5]. The information published by the services is collected by a Site-BDII, a service deployed in every site in EGI. The Site-BDIIs are queried by the Top-BDIIs - a national or regional located level of the hierarchy, which contain the information of all the site services available in the infrastructure and their services. NGIs usually provide an authoritative instance of Top-BDII, but every Top-BDII, if properly configured, should contain the same set of information.
Resource Providers must provide a Site-BDII endpoint that published information on the available resource following the GLUE2 schema. Even if the GLUE2 schema defines generic computing and storage entities, it was developed originally for Grid resources and can represent only partially the information needed by the Cloud users. Thus, the EGI Federated Cloud is working within the GLUE2 WG at OGF to profile and extend the schema to represent Cloud Computing, Storage and in the future Platform and Software services. The proposed extensions are currently under discussion at the WG.
EGI provides an implementation for service-level information that generates information supporting OpenStack and OpenNebula, Synnefo support is currently being added. The information is published in a different subtree (Glue2GroupID=cloud) so it can coexist with grid information and is easily discoverable by users.
Information available for each provider:
- Cloud computing resources
- Service endpoint
- Capabilities provided by the service, such as: virtual machine management or snapshot taking. The labels that identify the capabilities are agreed within the taskforce.
- Interface, the type of interface – e.g. webservice or webportal – and the interface name and version, for example OCCI 1.2.0
- User authentication and authorization profiles supported by the service, e.g. X.509 certificates
- Virtual machines images made available by the cloud provider
- Resource templates (number of cores and physical memory) allocable in a virtual machine.
Central service registry: GOCDB
EGI’s central service catalogue is used to catalogue the static information of the production infrastructure topology. The service is provided using the GOCDB tool that is developed and deployed within EGI. To allow Resource Providers to expose Cloud resources to the production infrastructure, a number of new service types were added to GODCB:
eu.egi.cloud.accountingeu.egi.cloud.storage-management.cdmieu.egi.cloud.vm-management.occi.eu.egi.cloud.vm-metadata.marketplaceeu.egi.cloud.vm-metadata.vmcatchereu.egi.cloud.vm-metadata.appdb-vmcaster
Special rules apply for the following service types:
- eu.egi.cloud.storage-management.cdmi: Endpoint URL field must contain the following info:
http[s]://hostname:port
- eu.egi.cloud.vm-management.occi: Endpoint URL field must contain the following info:
https://hostname:port/?image=<image_name>&resource=<resource_name>
Both <image_name> and <resource_name> cannot contain spaces. These attributes map to the OCCI os_tpl and resource_tpl respectively.
Higher level broker services also have its own service types:
eu.egi.cloud.broker.compsseu.egi.cloud.broker.proprietary.slipstreameu.egi.cloud.broker.vmdirac
Further information about GOCDB can be find on the following page: GOCDB/Input System User Documentation.
Monitoring: SAM
Services in the EGI infrastructure are monitored via SAM (Service Availability Monitoring). Specific probes to check functionality and availability of services must be provided by service developers, The current set of probes used for monitoring cloud resources consists of:
- OCCI probes (eu.egi.cloud.OCCI-VM and eu.egi.cloud.OCCI-Context): OCCI-VM creates an instance of a given image by using OCCI, checks its status and deletes it afterwards. OCCI-Context checks that the OCCI interfaces correctly supports the standard and the FedCloud contextualization extension.
- Accounting probe (eu.egi.cloud.APEL-Pub): Checks if the cloud resource is publishing data to the Accounting repository
- TCP checks (org.nagios.Broker-TCP, org.nagios.CDMI-TCP, org.nagios.OCCI-TCP and org.nagios.CloudBDII-Check): Basic TCP checks for services.
- VM Marketplace probe (eu.egi.cloud.AppDB-Update): gets a predetermined image list from AppDB and checks its update interval.
- Perun probe (eu.egi.cloud.Perun-Check): connects to the server and checks the status by using internal Perun interface
Probes for CDMI and the image synchronization mechanism are currently under development. More information on cloud probes can be at Cloud SAM tests.
Currently a central SAM instance specific to the activities of the EGI Federated Clouds Task has been deployed for monitoring test bed Results of cloud probes are visible on the central SAM interface under profile ch.cern.sam-CLOUD-MON and ch.cern.sam-CLOUD-MON_CRITICAL.
Accounting
EGI Federated Cloud has agreed on a Cloud Usage Record -which inherits from the OGF Usage record [6]- that defines the data that resource providers must send to EGI’s central Accounting repository. The Usage Record contains the following fields:
| Key | Value | Description | Mandatory |
|---|---|---|---|
| TO BE FILLED BY ACCOUNTING SCENARIO |
Support for retrieving the accounting data in this format is available from:
- OpenNebula: https://github.com/EGI-FCTF/opennebula-cloudacc
- Openstack – https://github.com/IFCA/caso
- Synnefo provides its own internal component
Once generated, records are delivered via the network of EGI message brokers to the central accounting repository using APEL SSM (Secure STOMP Messenger) provided by STFC. SSM client packages can be obtained at https://apel.github.io. A Cloud Accounting Summary Usage Record has also been defined and summaries created on a daily basis from all the accounting records received from the Resource Providers are sent to the EGI Accounting Portal. The EGI Accounting Portal also runs SSM to receive these summaries and provides a web page displaying different views of the Cloud Accounting data received from the Resource Providers.
References
- ↑ R. Nyren, A. Edmonds, A. Papaspyrou, and T. Metsch, Open Cloud Computing Interface - Core, GFD-P-R.183, April 2011. [Online]. Available: http://ogf.org/documents/GFD.183.pdf
- ↑ T. Metsch and A. Edmonds, Open Cloud Computing Interface - HTTP Rendering, GFD-P-R.185, April 2011. [Online]. Available: http://ogf.org/documents/GFD.185.pdf
- ↑ Open Cloud Computing Interface - Infrastructure, GFD-P-R.184, April 2011. [Online]. Available: http://ogf.org/documents/GFD.184.pdf
- ↑ SNIA Cloud Data Management Interface. http://www.snia.org/cloud
- ↑ GLUE Specification V2.0, GFD-R-P.147, March 2009.http://www.ogf.org/documents/GFD.147.pdf
- ↑ R. Mach, R. Lepor-Metz, S.Jackson, L.McGinnis, "Usage Record - Format Recommendation", GFD-R-P.098, https://www.ogf.org/documents/GFD.98.pdf