EGI CSIRT:Security challenges
| Mission | Members | Contacts
| Incident handling | Alerts | Monitoring | Security challenges | Procedures | Dissemination
Security challenges: what is it about ?
The goal of security drills, is to investigate whether sufficient information is available to be able conduct an audit trace as part of an incident response, and to ensure that appropriate communications channels are available.
EGI-CSIRT action on this thematic is at two points: - development of drills framework. They are available for egi sites; this is to help them verify their security maturity. - challenges at egi levels. Some wide level security challenge campaign are organized; this contributes to security at project level.
Security challenges: what is expecting from sites ?
What is important to bear in mind ?
The sites contacted for a challenge are asked to follow the normal security incident response procedure, and react as if the incident was real, with the two following exceptions:
1. No sanctions must be applied against the Virtual
Organization (VO) that was used to submit the job.
2. All "multi-destination" alerts must be addressed to
the e-mail list which has been designated for the test:
ssc-monitor@zwaan.nikhefhousing.nl
DO NOT use:
abuse@egi.eu
for Security Service Challenges. Instead, insert the
originally intended "multi-destination" address(es) in
the body of your message.
Information to be gathered at the sites
For an initial response and first directions answers to the following questions might be useful.
- NETWORK:
- Are there any other suspicious connections open? If so to which IPs - Is network monitoring data (e.g. netflows) available?
- CONTAINMENT:
- Does the process belong to a batch job or an interactive login? - From where was the login/job submission done? - In case it is a Grid-Job, the following questions are important: -To which VO is the user/certificate affiliated? - Which grid-certificates (DN) are involved in this test-incident? # Example: DN-1: CN=John Doe, O=<SomeInstitute>,O=<Something>, ..." - Since when were the jobs running? # Example: YYYY:MM:DD hh:mm Date:
The sites should provide the security teams asap with this information at latest within one working day.
The time needed to pass this information to EGI-CSIRT by replying to the alarm mail will be measured and evaluated.
Replying to the alarm mail will automatically use the above sketched RTIR system.
What is the normal security incident response procedure?
PLEASE REMIND THAT FOR THE CHALLENGE
THE PROCEDURE IS APPLIED WITH RESTRICTIONS
STATED IN THE PREVIOUS SECTION
The site checklist for incident response procedure is :
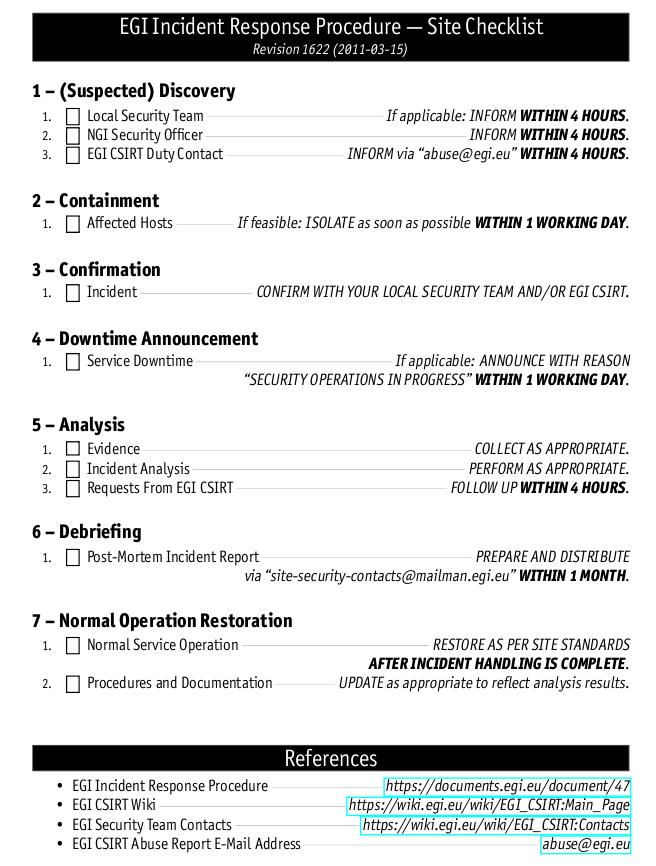
More informations about EGI security procedures ( flowchart, formal document, ... ) can be found here : https://wiki.egi.eu/wiki/EGI_CSIRT:Policies
Evaluation - Report generation
We distinguish between
1) Measurable per site operations (with target times):
- initial feedback: 4h
- found malicious job/processes/stop them: 4h
- ban problematic certificate: 8h
- contain the malicious binary and sent it to the incident-coordinator: 24h
These will be measured by the ssc-monitor and the points the sites get are calculated according to the formula stated on the wiki page. Times are relative to the alarm to the site, we try to make sure that the alarms will be send during office-hours (09:00 - 18:00, local time). The target times might change, will be in the final version on the wiki page.
2) Collaborative investigations: Since we want to achieve cross site communication, and possibly collaboration on the "malware" forensics the evaluation schema has changed accordingly. I..e Network forensics are needed, but we don't measure this, since due to the overall SSC set-up, most of this information should already be available to the "more western" sites relative to the initially alarmed sites.
ban/unban of the pilot-job-submitter DN is based on local policies. It will not be measured, but a statement on the decision, whether to ban/unban the pilot-job-submitter or not, is expected.
Security challenge: how is it operated ?
Tools
A framework has been developped to automate the operation of EGI security challenges.
The release of may 2011 contains: the panda framework for job submission, a prototype of the new EGI-CSIRT ticketing system based on RTIR.
The test malware is not intrusive, it does not try to get elevated priviledges.
More informations about the framework are given at security drills framework.
Post processing, clean up
As part of the incident handling, Grid authorizations may have been withdrawn from the DN that was used to submit the job. When the incident response procedure is complete, the test operator will explicitly request restoration of any such authorizations to their original state.
De-briefing
When the challenge has been completed on a representative number of Sites, the test operator will ask for de-briefing input from the participating Sites. Material submitted will be used to edit a report. The report will be circulated to the contributors for comments before being presented to the EGI-CSIRT.